Anti-Virus
Essentially
used to prevent, detect and remove malicious computer viruses. Most of
them also work well against other types of malware: browser hijackers,
ransomware, keyloggers, backdoors, rootkits, trojan horses, worms, among
others.
1.AMaViS
2.AVG Free
3.ClamAV
4.Avast!
5.P3Scan
Anti-Malware
Essentially
provide real time protection against the installation of malware
software on a computer. This type of malware protection works the same
way as that of antivirus protection in that the anti-malware software
scans all incoming network data for malware and blocks any threats it
comes across.
6.chkrootkit
7.Nixory
8.rkhunter
9.OSSEC
Encryption
Essentially
a process of encoding messages or information in such a way that only
authorised parties can read it. Encryption does not of itself prevent
interception, but denies the message content to the interceptor.
10.GnuPG
11.MCrypt
12.OpenSignature
13.PeaZip
14.Stunnel
15.MailCrypt
Intrusion Detection
Essentially
monitors network or system activities for malicious activities or
policy violations and produces reports to a management station.
16.AFICK
17.Bro
18.Kismet
19.Sguil
20.Snort
21.Tripwire
Firewalls
Essentially
a network security system that controls the incoming and outgoing
network traffic based on applied rule set. A firewall establishes a
barrier between a trusted, secure internal network and another network
that is not assumed to be secure and trusted.
22.FireHOL
23.Firestarter
24.Netfilter
25.IPCop
26.Shorewall
27.Turtle Firewall
Network Monitoring
Essentially
monitors a computer network for slow or failing components and notifies
the network administrator (via email, SMS or other alarms) in case of
outages.
28.Argus
29.Nagios
30.Nipper
31.ntop
32.SniffDet
33.tcpdump
Network Traffic Analyser
Essentially
intercepts and examins messages in order to deduce information from
patterns in communication. It can be performed even when the messages
are encrypted and cannot be decrypted.
34.dsniff
35.ngrep
36.Ettercap
37.Wireshark
Packet Crafting
Essentially
allows network administrators to probe firewall rule-sets and find
entry points into a targeted system or network by manually generating
packets to test network devices and behaviour.
38.Nemesis
39.Hping3
40.Scapy
41.Yersinia
Vulnerability Scanner
Essentially designed to assess computers, computer systems, networks or applications for weaknesses.
42.Nessus
43.SARA
44.Tiger
Log File Analysers
Essentially used to make sense out of computer-generated records (also called log or audit trail records).
45.AWStats
46.tcpreplay
47.The Webaliser
VPN Tools
Essentially
enables a computer to send and receive data across shared or public
networks as if it is directly connected to the private network, while
benefiting from the functionality, security and management policies of
the private network.
48.Poptop
49.SSL Explorer
50.OpenVPN
Source: Linux Links
About IT
Thursday, June 4, 2015
Thursday, May 21, 2015
PDF tools : convert html to pdf on the fly
HTML To PDF Converter:
It's not a very easy job to extract content from a webpage if you are not using an appropriate tool. Most often you need to extract information directly from the Internet browser. Then this converter comes to help as it creates a PDF file of the required webpage for future usage. This tool is also useful for language applications.
PDFonFly:
This is a free online converter which takes the URL of a web page and converts it into a PDF file. Text can also be entered into WYSIWYG text field and then it's turned to a PDF file as well. At the bottom of every page, a two-line footer is generated too.
PDFCrowd:
This is a free online converter which takes a URL, an HTML file or even direct HTML input and convert them into a PDF file. Then the file is downloaded to your computer. It also adds a footer to each page with a logo and an advertisement. This tool allows customisation too.
Web2PDFConvert:
This is another online solution which installs a PDF convert button and it can make everything in a single click. It also has a unique feature which converts HTML via email by sending the recipient a webpage in a portable document format.
PDF2HTML Online:
It's known for its capability of extracting images into a separate directory. It can also write HTML4 and keep the hyperlinks which are present in the PDF file. It's an online tool which involves an easy conversion procedure too.
It's not a very easy job to extract content from a webpage if you are not using an appropriate tool. Most often you need to extract information directly from the Internet browser. Then this converter comes to help as it creates a PDF file of the required webpage for future usage. This tool is also useful for language applications.
PDFonFly:
This is a free online converter which takes the URL of a web page and converts it into a PDF file. Text can also be entered into WYSIWYG text field and then it's turned to a PDF file as well. At the bottom of every page, a two-line footer is generated too.
PDFCrowd:
This is a free online converter which takes a URL, an HTML file or even direct HTML input and convert them into a PDF file. Then the file is downloaded to your computer. It also adds a footer to each page with a logo and an advertisement. This tool allows customisation too.
Web2PDFConvert:
This is another online solution which installs a PDF convert button and it can make everything in a single click. It also has a unique feature which converts HTML via email by sending the recipient a webpage in a portable document format.
PDF2HTML Online:
It's known for its capability of extracting images into a separate directory. It can also write HTML4 and keep the hyperlinks which are present in the PDF file. It's an online tool which involves an easy conversion procedure too.
Monday, December 3, 2012
Windows 8 Licenses
Preinstalled licenses for Windows 8 use the new OA3.0, so I guess no COA
sticker. I was thinking Windows 7 for some reason. I forgot what forum I
was in for a second there.
The BIOS contains a hash that tells the Windows 8 installer that it is licensed for a specific version of Windows 8 (Windows 8 or Windows 8 Pro). If you install (or reinstall) that licensed version, it simply "activates" because the hardware is activated for that version of Windows. If you install a version of Windows 8 that the hardware isn't licensed for, it won't activate automatically and you'll have to put in a product key.
The BIOS will have a SLIC table that is used for OEM-SLP activation. The big OEM's like Dell etc, add the custom SLIC table to their BIOS. The OEM installed OS looks for the SLIC table and if its found and matches a corresponding certificate file Activation is automatic. If it can't find the correct SLIC table activation fails. OEM-SLP does not activate online. If you create recovery media the OEM-SLP activation will be preserved for the PC its created on. You can't READ the OEM-SLP Product Code from the BIOS. Not without a utility anyway. You can use a utility like the Magical Jelly Bean Key Finder to retrieve it from the installed OS. Its not of any use though because OEM-SLP keys will not activate online. Every DELL model XYZ will have the same OEM-SLP product code and that code is blocked from online activation. That's why those PC's also have a COA sticker on them. If you have to you can install with a regular OEM DVD and use the Product code on the COA sticker. windows 7 uses OA 2.1. Windows 8 uses a new OA 3.0. With OA 3.0 each PC has a unique SLP product code that is embedded in its BIOS. One of the tricks used to pirate Windows was to add a SLIC table to a PC's BIOS so you could fake OEM-SLP activation. OA 3.0 is designed to prevent this and make it harder to pirate Windows. I'm sure there is more to it than that but the rest of it is a bit over my head. I would think there should still be a COA sticker on a Windows 8 machine though. How are you supposed to install the OS without the recovery disks? With OA 3.0 I would think the recovery media would only work on the PC it was created on. It would be unique to that PC not just to that make and model like it is now.
The BIOS contains a hash that tells the Windows 8 installer that it is licensed for a specific version of Windows 8 (Windows 8 or Windows 8 Pro). If you install (or reinstall) that licensed version, it simply "activates" because the hardware is activated for that version of Windows. If you install a version of Windows 8 that the hardware isn't licensed for, it won't activate automatically and you'll have to put in a product key.
The BIOS will have a SLIC table that is used for OEM-SLP activation. The big OEM's like Dell etc, add the custom SLIC table to their BIOS. The OEM installed OS looks for the SLIC table and if its found and matches a corresponding certificate file Activation is automatic. If it can't find the correct SLIC table activation fails. OEM-SLP does not activate online. If you create recovery media the OEM-SLP activation will be preserved for the PC its created on. You can't READ the OEM-SLP Product Code from the BIOS. Not without a utility anyway. You can use a utility like the Magical Jelly Bean Key Finder to retrieve it from the installed OS. Its not of any use though because OEM-SLP keys will not activate online. Every DELL model XYZ will have the same OEM-SLP product code and that code is blocked from online activation. That's why those PC's also have a COA sticker on them. If you have to you can install with a regular OEM DVD and use the Product code on the COA sticker. windows 7 uses OA 2.1. Windows 8 uses a new OA 3.0. With OA 3.0 each PC has a unique SLP product code that is embedded in its BIOS. One of the tricks used to pirate Windows was to add a SLIC table to a PC's BIOS so you could fake OEM-SLP activation. OA 3.0 is designed to prevent this and make it harder to pirate Windows. I'm sure there is more to it than that but the rest of it is a bit over my head. I would think there should still be a COA sticker on a Windows 8 machine though. How are you supposed to install the OS without the recovery disks? With OA 3.0 I would think the recovery media would only work on the PC it was created on. It would be unique to that PC not just to that make and model like it is now.
Tuesday, October 23, 2012
Office 2013 RTM at Build 15.0.4420.1017
Office 2013 RTM at Build 15.0.4420.1017
Microsoft has announced that Office 2013, the most popular office productivity suite, has been released to manufacturing (RTM). It means that the development on Office 2013 has generally completed.Windows RT users will probably get to use Office 2013 earlier than anyone else (unless of course you’re Microsoft insiders or there is a leak), as Windows RT devices will ship with the preview version of Office Home & Student 2013 RT from Windows 8 launch date, October 26th, 2012, but will be upgraded to full RTM version in early November. Office Home & Student 2013 RT includes the new Word, Excel, PowerPoint and OneNote applications for Windows RT devices.
Some business customers will get their hand on final build of Office 2013 earlier than others, as early as November 2012. According to Office News, Office 365 Enterprise customers will be using Office 2013 from the next service update starting in November through general availability. Volume Licensing customers with Software Assurance will be able to download the Office 2013 applications as well as other Office products including SharePoint 2013, Lync 2013 and Exchange 2013 through the Volume Licensing Service Center by mid-November, while IT professionals and developers will be able to download the final version via their TechNet or MSDN subscriptions by mid-November.
The general availability of Office 2013 is planned for the first quarter of 2013.
While Microsoft does not announce what’s the final build version for the Office 2013 RTM, some lucky folks have managed to download and install Office 2013 RTM. According to a Chinese blog, the build version for Office 2013 RTM is 15.0.4420.1017. The preview version of Office 2013 released by Microsoft has the build number of 15.0.4128.1014.
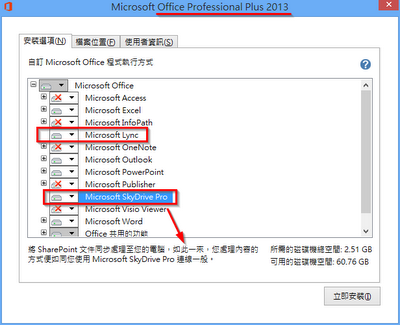
Comparing with Office 2010, Office 2013 has integrated Microsoft Lync 2013, which was previously a separate download, and Microsoft SkyDrive Pro, which allows business users to access, save and share files and documents through SharePoint. Essentially SkyDrive Pro is doing what SkyDrive does for home users, may be replacing SharePoint Workspace.
Related Posts:
- Download MS Office 2010 Build 14.0.4730.1007 (x86 and x64)
- Microsoft Office 2010 Beta 2 Build 14.0.4514.1007 Download (with Project and Visio)
- MS Office 2010 RC (RTM Escrow) Build 4734.1000 Released in Connect to TAP Members
- Office 2010 RC (RTM Escrow) VLK Build 14.0.4734.1000 (with Visio and Project) Free Download
- Office 2011 for Mac OS X Beta 2 Build 14.0.0.100326 Leaked Download with Serial Key
Security and the Cloud
Security and the Cloud – Part 1
This will be the first of a number of op-ed pieces on the security
landscape of cloud computing. Security is often quoted as one of the
main reason people back away from embracing the cloud. This I believe is
often due to a combination of an over estimation of how secure their
current arrangements are and a lack of knowledge about how secure the
cloud CAN be. In this last regard the cloud is nothing special, like
every other application, database or service its security is largely
dependant on how it is used and configured and not its inherent
capabilities.
As a step in gaining an understanding of the subject lets break the security landscape down into a number of arenas and look at how a classical on premise data centre, compares with an IaaS based cloud offering. This analysis can be extended to other scenarios but this is an informative example.
The physical arena, covers a direct attack on the equipment. If someone can actually walk up and touch the server then generally you have already lost. Encryption can help but that is very much a silver lining.
- Home Data Centre :- In a small regional facility with limited physical security as all the cost of security is borne by a single operator.
- Cloud IaaS:- Most likely state of the art security and a dedicated physical security team. Total cost of all security is borne across ALL the global clients of the provider.
‘Pipes’ arena, (apologies for the badly overused phrase), data and applications on a server are useless unless people can connect into them. This arena covers everything between the users device and the login screen.
- Home Data Centre:- Physical links into main offices, extremely secure provision of service to everyone at a desk. Mobile access has potentially been bolted on and is an increasingly overused tactical fix as the strategic solution is yet to be implemented.
- Cloud IaaS:- Mobile and Office users are in the same boat, you can’t have a tactical solution here and must expend the time and resources needed to create a fully secure strategic solution.
So I saved the best till last the users arena, again this is a no score draw between the two offerings as its the same users using the applications no matter where they are hosted. However it is worth thinking long and hard about how, where and on what users are working.
User arena security items are probably far bigger weak points then any other aspect of security in the modern environment. Sophisticated technology based attacks using zero day exploits make the news and are currently beating nation state security, but for everyone of these attacks there are hundreds based on social attacks on users. It doesn’t matter how complex and complete the lock is if someone can borrow a key.
A move to the cloud offers many benefits and can generally be made as secure as current on premise solutions. Focus should be spent on ensuring the your VPN, mobile and remote technology solutions are geared up to handle the increased traffic and are fully thought out strategic choices. However conversation on “how secure the cloud is” are great starting points to re-engage the business in the day to day activities and practices that make your data and applications stay secure independent of where they are delivered from.
As a step in gaining an understanding of the subject lets break the security landscape down into a number of arenas and look at how a classical on premise data centre, compares with an IaaS based cloud offering. This analysis can be extended to other scenarios but this is an informative example.
The physical arena, covers a direct attack on the equipment. If someone can actually walk up and touch the server then generally you have already lost. Encryption can help but that is very much a silver lining.
- Home Data Centre :- In a small regional facility with limited physical security as all the cost of security is borne by a single operator.
- Cloud IaaS:- Most likely state of the art security and a dedicated physical security team. Total cost of all security is borne across ALL the global clients of the provider.
‘Pipes’ arena, (apologies for the badly overused phrase), data and applications on a server are useless unless people can connect into them. This arena covers everything between the users device and the login screen.
- Home Data Centre:- Physical links into main offices, extremely secure provision of service to everyone at a desk. Mobile access has potentially been bolted on and is an increasingly overused tactical fix as the strategic solution is yet to be implemented.
- Cloud IaaS:- Mobile and Office users are in the same boat, you can’t have a tactical solution here and must expend the time and resources needed to create a fully secure strategic solution.
This is where the CAN statement comes in, a Cloud based
solution could be offer greater security than your home solution but
only if it is build correctly.
Applications arena, this is a non score draw scenario as its
the same applications in both locations. However this is an important
arena as using other types of cloud solution such as SaaS and PaaS mean
very different applications between the cloud and non cloud based
services.So I saved the best till last the users arena, again this is a no score draw between the two offerings as its the same users using the applications no matter where they are hosted. However it is worth thinking long and hard about how, where and on what users are working.
User arena security items are probably far bigger weak points then any other aspect of security in the modern environment. Sophisticated technology based attacks using zero day exploits make the news and are currently beating nation state security, but for everyone of these attacks there are hundreds based on social attacks on users. It doesn’t matter how complex and complete the lock is if someone can borrow a key.
A move to the cloud offers many benefits and can generally be made as secure as current on premise solutions. Focus should be spent on ensuring the your VPN, mobile and remote technology solutions are geared up to handle the increased traffic and are fully thought out strategic choices. However conversation on “how secure the cloud is” are great starting points to re-engage the business in the day to day activities and practices that make your data and applications stay secure independent of where they are delivered from.
Friday, August 3, 2012
Windows 8 RTM at Build 9200
Microsoft has officially announced that Windows
8 and its server version, Windows Server 2012, and the whole related
ecosystem has been released to manufacturing (RTM), which indicated that
the development of the OS has been completed, and the final code has
already been handled to OEM partners for the purpose of preloading and
preinstalling Windows 8 onto products sold to end-users.
The final build for Windows 8 RTM is build 9200, and build string is said to be version 6.2 and 9200.16384.win8_rtm.120725-1247, indicating the build was signed off on July 25th, 2012.
Windows Team blog published the schedule for Windows 8 release that specified who will be able to download Windows 8 at when.
The RTM of Windows 8 also signifies that Internet Explorer 10 (IE10) and Windows Store RTM is opened for business. However, a RTM build of Windows 8 is required to upload apps to the Store. Final build of Visual Studio 2012 will also be released on August 15th from MSDN.
Windows Server 2012, the so called Cloud OS, will available for everyone on September 4th, 2012.
Discuss the Windows 8 RTM milestone at the forum.
64-bit version of Windows 8 Enterprise N has leaked.
No related posts.
The final build for Windows 8 RTM is build 9200, and build string is said to be version 6.2 and 9200.16384.win8_rtm.120725-1247, indicating the build was signed off on July 25th, 2012.
Windows Team blog published the schedule for Windows 8 release that specified who will be able to download Windows 8 at when.
- August 15: MSDN and TechNet subscribers will be the first to get access to the new software.
- August 16: Software Assurance customers and Microsoft Partner Network members will get access to the operating system.
- August 20: Microsoft Action Pack providers will be given Windows 8.
- September 1: Volume license customers not using Software Assurance will be able to purchase Windows 8 licenses.
- October 26: Retail copies of Windows 8 and PCs and tablets (including Microsoft’s own Surface tablet) will go on sale.

The RTM of Windows 8 also signifies that Internet Explorer 10 (IE10) and Windows Store RTM is opened for business. However, a RTM build of Windows 8 is required to upload apps to the Store. Final build of Visual Studio 2012 will also be released on August 15th from MSDN.
Windows Server 2012, the so called Cloud OS, will available for everyone on September 4th, 2012.
Discuss the Windows 8 RTM milestone at the forum.
64-bit version of Windows 8 Enterprise N has leaked.
No related posts.
Subscribe to:
Posts (Atom)

